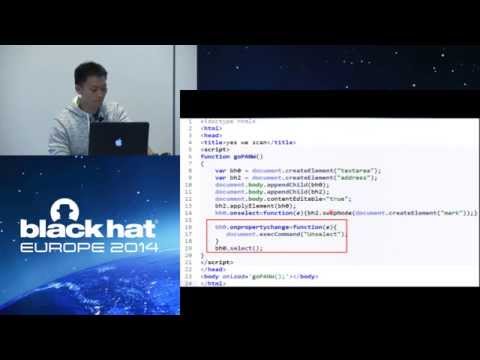
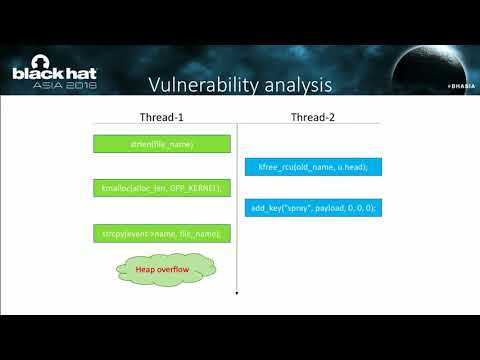
#Use-After-Free Vulnerability
Showing: 12 courses
1 Lesons
47 minutes
On-Demand
Free-Video
5 Lesons
6 hours 12 minutes
On-Demand
Free-Video
18 Lesons
46 minutes
On-Demand
Free-Video
1 Lesons
35 minutes
On-Demand
Free-Video
16 Lesons
35 minutes
On-Demand
Free-Video
7 Lesons
38 minutes
On-Demand
Free-Video
21 Lesons
32 minutes
On-Demand
Free-Video
27 Lesons
34 minutes
On-Demand
Free-Video
1 Lesons
47 minutes
On-Demand
Free-Video
1 Lesons
57 minutes
On-Demand
Free-Video
1 Lesons
44 minutes
On-Demand
Free-Video
1 Lesons
35 minutes
On-Demand
Free-Video