Description:
Explore a powerful browser fuzzing strategy that uncovered over 100 Internet Explorer use-after-free vulnerabilities in this 34-minute Black Hat conference talk. Learn about the custom-built vulnerability hunting system and unique fuzzing approach that led to 19 CVEs affecting all versions of Microsoft IE. Discover the importance of effective fuzzing strategies in finding critical browser vulnerabilities, and gain insights into the methodology behind explicit and implicit pairing techniques. Examine the implementation, experimentation, and results of this innovative approach to browser security testing, and consider its implications for future vulnerability research.
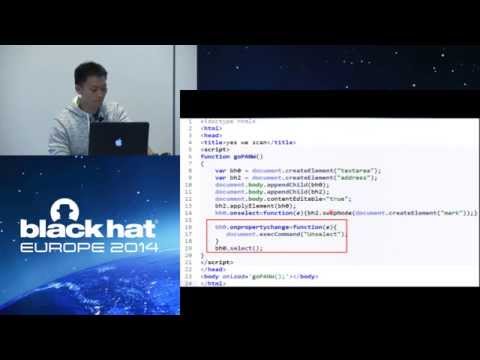
The Power of Pair - One Template that Reveals 100+ UAF IE Vulnerabilities
Add to list
#Conference Talks
#Black Hat
#Programming
#Software Development
#Information Security (InfoSec)
#Ethical Hacking
#Cybersecurity
#Web Security
#Browser Security
#Computer Security
#Memory Safety
#Use-After-Free Vulnerability