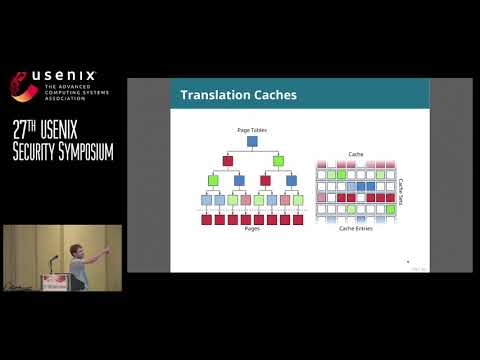
#Cache Attacks
Showing: 16 courses
18 Lesons
17 minutes
On-Demand
Free-Video
14 Lesons
17 minutes
On-Demand
Free-Video
21 Lesons
17 minutes
On-Demand
Free-Video
11 Lesons
20 minutes
On-Demand
Free-Video
23 Lesons
29 minutes
On-Demand
Free-Video
1 Lesons
1 hour 9 minutes
On-Demand
Free-Video
1 Lesons
46 minutes
On-Demand
Free-Video
1 Lesons
33 minutes
On-Demand
Free-Video
37 Lesons
54 minutes
On-Demand
Free-Video
14 Lesons
23 minutes
On-Demand
Free-Video
1 Lesons
49 minutes
On-Demand
Free-Video
1 Lesons
23 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video
1 Lesons
1 hour 23 minutes
On-Demand
Free-Video
1 Lesons
1 hour 4 minutes
On-Demand
Free-Video
1 Lesons
12 minutes
On-Demand
Free-Video