Description:
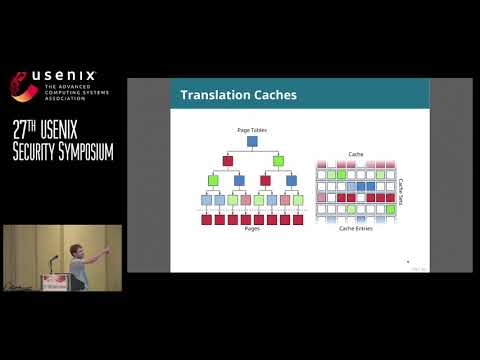
Explore a groundbreaking presentation from USENIX Security '18 that challenges existing software-based defenses against cache attacks. Delve into the concept of indirect cache attacks, focusing on the Malicious Management Unit (MMU) as a potential vector for bypassing current security measures. Learn about the vulnerabilities in cache access isolation techniques and the complexities of mitigating arbitrary cache attacks. Examine the PRIME + PROBE method, page coloring, XLATE attacks, page table walks, and translation caches. Investigate the challenges of building eviction sets, reliability concerns, and the effectiveness of current cache defenses. Gain valuable insights into why stopping cache attacks in software is more difficult than previously thought, and understand the implications for future security strategies in computer systems.
Malicious Management Unit - Why Stopping Cache Attacks in Software is Harder Than You Think
Add to list
#Conference Talks
#USENIX Security
#Information Security (InfoSec)
#Cybersecurity
#Software Security
#Computer Security
#Cache Attacks