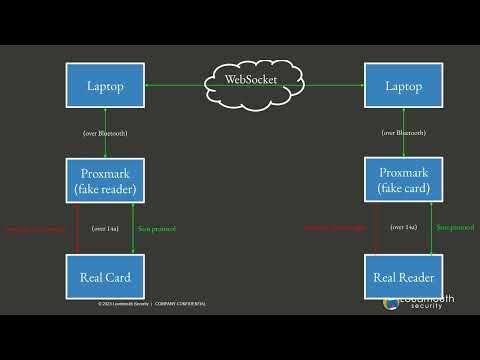
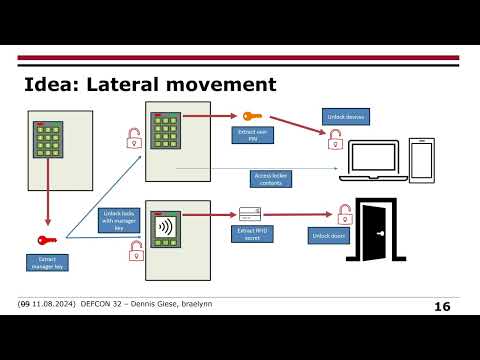
#RFID
Showing: 20 courses
31 Lesons
1 day 4 hours
On-Demand
Free-Video
45 Lesons
44 minutes
On-Demand
Free-Video
12 Lesons
40 minutes
On-Demand
Free-Video
1 Lesons
49 minutes
On-Demand
Free-Video
12 Lesons
44 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video
1 Lesons
53 minutes
On-Demand
Free-Video
11 Lesons
28 minutes
On-Demand
Free-Video
23 Lesons
37 minutes
On-Demand
Free-Video
15 Lesons
52 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video
1 Lesons
23 minutes
On-Demand
Free-Video
1 Lesons
17 minutes
On-Demand
Free-Video
1 Lesons
21 minutes
On-Demand
Free-Video
1 Lesons
45 minutes
On-Demand
Free-Video
1 Lesons
38 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video
8 Lesons
40 minutes
On-Demand
Free-Video
1 Lesons
49 minutes
On-Demand
Free-Video
1 Lesons
1 hour 1 minute
On-Demand
Free-Video