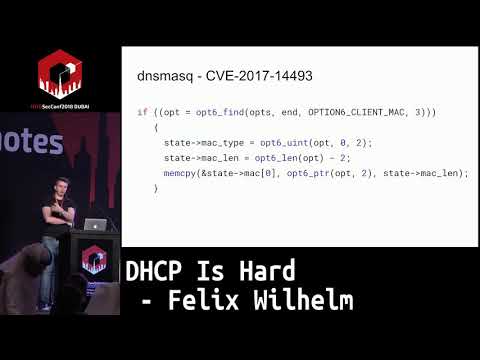
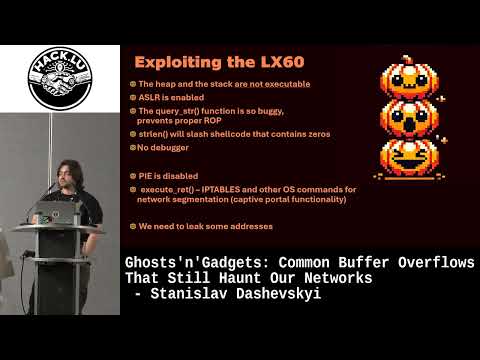
#Heap Overflows
Showing: 9 courses
1 Lesons
53 minutes
On-Demand
Free-Video
23 Lesons
42 minutes
On-Demand
Free-Video
1 Lesons
52 minutes
On-Demand
Free-Video
15 Lesons
48 minutes
On-Demand
Free-Video
20 Lesons
33 minutes
On-Demand
Free-Video
19 Lesons
51 minutes
On-Demand
Free-Video
1 Lesons
28 minutes
On-Demand
Free-Video
1 Lesons
53 minutes
On-Demand
Free-Video
30 Lesons
1 hour 5 minutes
On-Demand
Free-Video