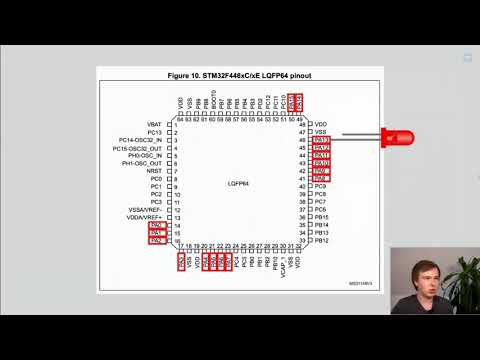
#Ghidra
Showing: 26 courses
6 Lesons
1 hour 30 minutes
On-Demand
Free-Video
17 Lesons
4 hours 30 minutes
On-Demand
Free-Video
7 Lesons
1 hour 30 minutes
On-Demand
Free-Video
8 Lesons
31 minutes
On-Demand
Free-Video
14 Lesons
1 hour 1 minute
On-Demand
Free-Video
8 Lesons
30 minutes
On-Demand
Free-Video
5 Lesons
1 hour 5 minutes
On-Demand
Free-Video
8 Lesons
53 minutes
On-Demand
Free-Video
8 Lesons
1 hour 1 minute
On-Demand
Free-Video
10 Lesons
1 hour
On-Demand
Free-Video
1 Lesons
31 minutes
On-Demand
Free-Video
1 Lesons
31 minutes
On-Demand
Free-Video
19 Lesons
46 minutes
On-Demand
Free-Video
1 Lesons
47 minutes
On-Demand
Free-Video
17 Lesons
44 minutes
On-Demand
Free-Video
31 Lesons
52 minutes
On-Demand
Free-Video
1 Lesons
1 hour
On-Demand
Free-Video
1 Lesons
1 hour 31 minutes
On-Demand
Free-Video
1 Lesons
37 minutes
On-Demand
Free-Video
1 Lesons
42 minutes
On-Demand
Free-Video
1 Lesons
22 minutes
On-Demand
Free-Video
31 Lesons
48 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video
1 Lesons
44 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video