Description:
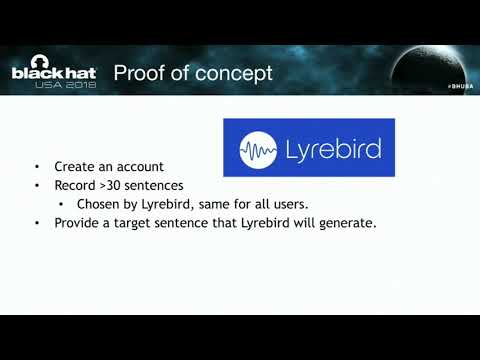
Explore the vulnerabilities of voice fingerprinting authentication in this 36-minute Black Hat conference talk. Delve into recent machine learning advancements enabling the generation of synthetic, high-quality audio using speech recordings. Learn about text-to-speech systems, open-source models like Tacotron and WaveNet, and techniques such as data augmentation and transfer learning. Understand the implications for financial institutions, home automation products, and hi-tech offices. Discover potential mitigation strategies, including multi-factor authentication and CGI detection. Gain insights into the broader context of machine learning in offensive security.
Your Voice is My Passport
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Machine Learning
#Transfer Learning
#Data Science
#Data Collection
#Multi-Factor Authentication
#Data Augmentation