Description:
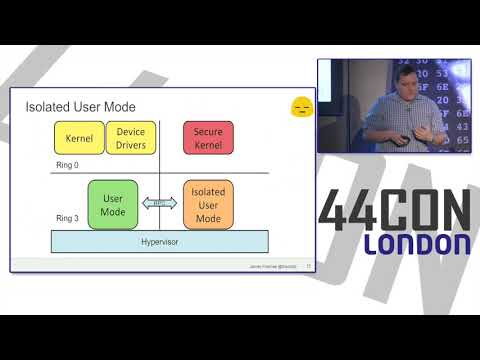
Explore the security landscape of Windows 10 in this 50-minute conference talk presented by James Forshaw at the 44CON Information Security Conference. Delve into the advanced security features of Windows 10, such as Control Flow Guard and Credentials Isolation, while examining the potential vulnerabilities that accompany these new additions. Gain insights into the challenges of secure engineering as Forshaw dissects local system vulnerabilities, service privilege levels, and isolated user mode. Analyze the security measures implemented in Microsoft Edge, including its handling of Flash content. Investigate User Account Control (UAC) mechanisms, focusing on auto-elevation processes and directory checks. Learn about Windows symbolic links, Win32k hardening, and process silos. Discover how changes in device object handling and root object directory replacement impact system security. Conclude with a public service announcement and reflections on the ongoing complexities of maintaining a secure operating system.
Read more
Windows 10 - 2 Steps Forward, 1 Step Back
Add to list
#Conference Talks
#44CON
#Personal Development
#Self Improvement
#Digital Skills
#Windows
#Windows 10
#Windows 10 Security