Description:
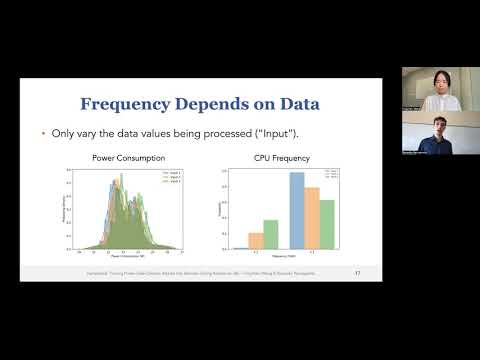
Explore the groundbreaking Hertzbleed attack in this conference talk, which transforms power side-channel attacks into remote timing attacks on x86 processors. Delve into the intricacies of Dynamic Voltage and Frequency Scaling (DVFS) on modern Intel CPUs and understand how frequency depends on power consumption. Examine data-dependent frequency variations and their implications for security. Investigate the frequency leakage model and its application to bit positions. Learn about the Supersingular Isogeny Key Encapsulation (SIKE) protocol and how it's vulnerable to adaptive chosen-ciphertext attacks. Analyze the remote timing attack model, discuss its implications, and explore potential mitigations for this novel security threat.
Hertzbleed: Turning Power Side-Channel Attacks Into Remote Timing Attacks on x86 - Session 3
Add to list
#Computer Science
#Cryptography
#Information Security (InfoSec)
#Cybersecurity
#Computer Security
#Side Channel Attacks