Description:
Explore VMware security vulnerabilities and escape techniques in this 47-minute conference talk from Derbycon 7. Dive into VMware architecture, backdoor PCI, and the Host Open exploit. Learn about the Ghost In The Shell technique, Metasploit module development, and a Deuse After Free attack. Gain insights into VMware escapology and hypervisor security through detailed explanations, demonstrations, and a comprehensive analysis of potential attack vectors.
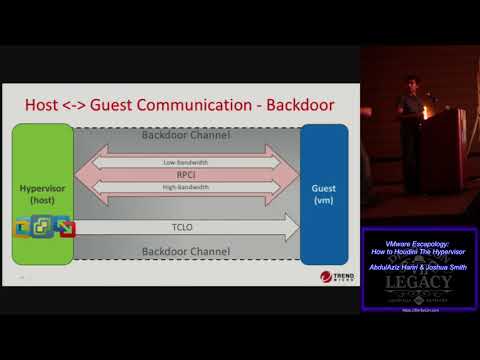
VMware Escapology - How to Houdini The Hypervisor
Add to list
#Conference Talks
#Information Security (InfoSec)
#Penetration Testing
#Metasploit
#Data Science
#Big Data
#Hadoop
#HDFS
#Cybersecurity
#PCI Compliance