Description:
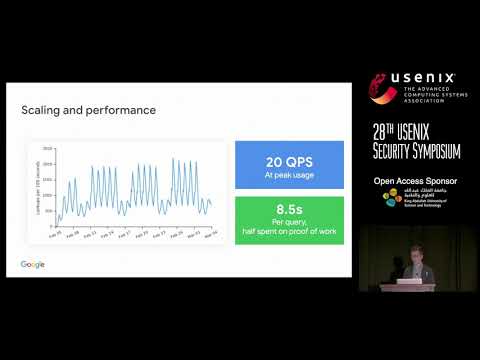
Explore a Distinguished Paper Award-winning conference talk from USENIX Security '19 that delves into a privacy-preserving protocol for protecting accounts from credential stuffing attacks. Learn about the asymmetry of knowledge between attackers and users, and discover how a centralized breach repository can be queried without compromising sensitive information. Examine the implementation of a cloud service accessing over 4 billion breached credentials and a Chrome extension client. Analyze findings from anonymous telemetry involving 670,000 users and 21 million logins, revealing that 1.5% of web logins use breached credentials. Understand the impact of breach alerts on user behavior, with 26% of warnings resulting in password changes. Explore the ethical considerations, principles, and challenges in designing this protocol, including private set intersection and denial of service prevention. Gain insights into Google's strategy, password security state, and the prevalence of credential stuffing threats across the internet.
Read more
Protecting Accounts from Credential Stuffing with Password Breach Alerting
Add to list
#Conference Talks
#USENIX Security
#Information Security (InfoSec)
#Cybersecurity
#Programming
#Cloud Computing
#Cloud Services
#Password Security
#Computer Science
#Computer Networking
#Protocol Design
#Web Development
#Browser Extensions
#Chrome Extensions
#Credential Stuffing