Description:
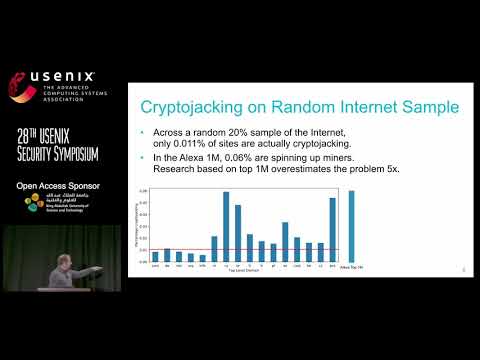
Explore a comprehensive study on cryptojacking campaigns at internet scale in this 21-minute conference talk from USENIX Security '19. Delve into the world of illicit cryptomining, examining its rise since 2017 and the methods criminals use to monetize websites. Learn about the identification of 204 cryptojacking campaigns, significantly more than previously estimated, and discover how third-party software like WordPress has become a primary vector for spreading infections. Gain insights into the popularity of mining applications through NetFlow data analysis, comparing Coinhive's installation base to CoinImp WebSocket proxies' traffic volume. Understand the prevalence of cryptojacking across the internet, with findings from a crawl of 49 million domains, and learn which website categories are most affected. Examine the anatomy of browser-based cryptomining, attack vectors, and methods for distinguishing cryptojacking services. Investigate how infections are linked to campaigns and explore key takeaways from this extensive research.
Read more
Inadvertently Making Cyber Criminals Rich - A Comprehensive Study of Cryptojacking Campaigns at Internet Scale
Add to list