Description:
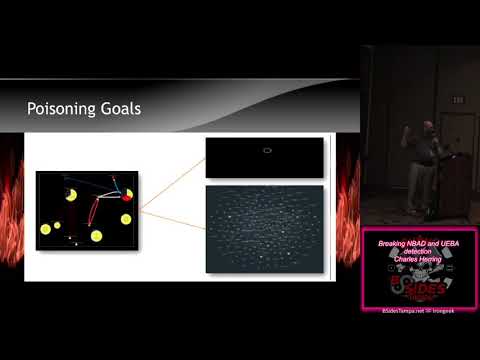
Explore techniques for circumventing Network Behavior Anomaly Detection (NBAD) and User and Entity Behavior Analytics (UEBA) in this 29-minute conference talk from BSides Tampa 2020. Delve into topics such as baselining, anomaly detection, data poisoning, and behavioral spoofing prevention. Learn about various tools and methods including pump and dump techniques, pocket dimensions, bridge networks, and UDP spraying. Gain insights on creating fake traffic, API curls, and baseline boiling. Conclude with an analysis of these techniques and discover remediation strategies to enhance network security.
Breaking NBAD and UEBA Detection
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Machine Learning
#Data Poisoning