Description:
Explore a cutting-edge paper on cryptographic implementation security presented at Eurocrypt 2020. Delve into the Tornado framework for automatically generating probing-secure masked bitsliced implementations. Learn about Satan attacks, masking techniques, and the Tornado pipeline. Understand the verification process and performance implications of this innovative approach to enhancing cryptographic security against side-channel attacks.
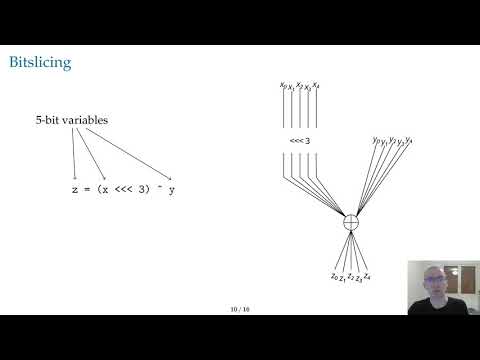
Tornado- Automatic Generation of Probing-Secure Masked Bitsliced Implementations
Add to list