Description:
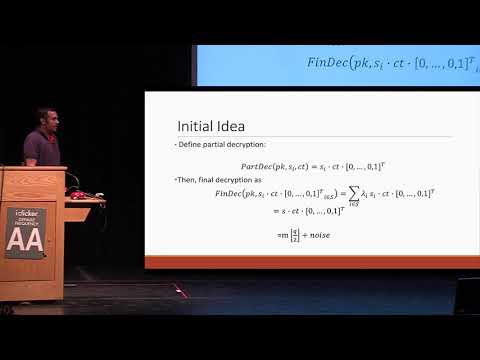
Explore a comprehensive presentation from Crypto 2018 on threshold cryptosystems derived from threshold fully homomorphic encryption. Delve into key concepts including character introduction, key management, threshold cryptography, signatures, and public key encryption. Examine the [GSW13] FHE scheme, noise smudging techniques, and solutions for noise blowup. Compare different schemes, investigate the expressiveness of {0,1}-LSSS, and learn about the universal thresholdizer. Discover practical applications of these techniques and consider open problems in the field of threshold cryptography.
Threshold Cryptosystems From Threshold Fully Homomorphic Encryption
Add to list