Description:
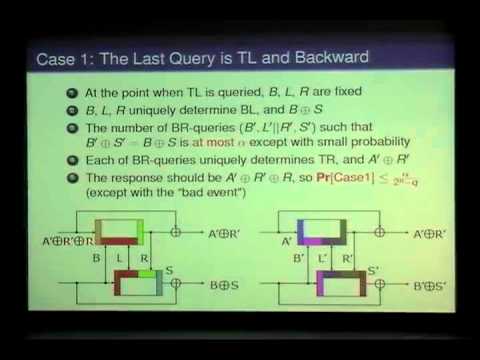
Explore the collision security of Tandem-DM in the Ideal Cipher Model through this 20-minute talk from Crypto 2011. Delve into the research by Martijn Stam, Joojoung Lee, and John Steinberger as they present their findings on this cryptographic topic. Begin with an introduction to the Ideal Cipher Model and query history before evaluating Tandem-DM and analyzing collisions within it. Examine various cases, including when the last query is TL and backward or forward, and understand the concept of a modified adversary A'. Gain insights into the properties of the modified adversary and discover the main results of this cryptographic analysis.
The Collision Security of Tandem-DM in the Ideal Cipher Model
Add to list