Description:
Explore the intricacies of the Domain Name System (DNS) in this 36-minute conference talk from Louisville InfoSec 2016. Delve into DNS operation, potential threats, and security intelligence with expert Tom Kopchak. Learn about amplification attack processes, proper DNS server configuration, and the importance of only providing responses for domains you own. Discover the dangers of blind transfers and domain hijacking, and explore effective countermeasures. Examine DNS security use cases, including SSL traffic correlation challenges and threat intelligence using DNS data. Gain insights into forensic investigations, DNS data exfiltration detection, and the role of DNS in threat intelligence research. Enhance your understanding of DNS security to better protect your organization's digital infrastructure.
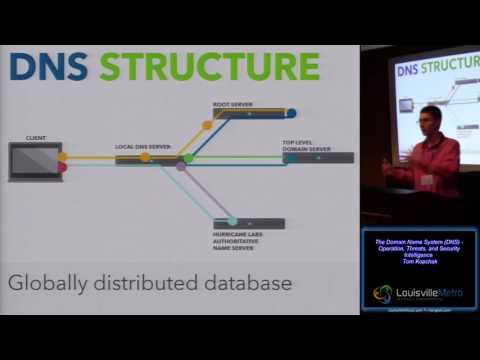
The Domain Name System - DNS Operation, Threats, and Security Intelligence
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Threat Intelligence
#Computer Science
#Computer Networking
#DNS
#Network Administration