Description:
Explore post-exploitation techniques in Metasploit with this conference talk from Derbycon 2012. Dive into the fundamentals of post-exploitation, its importance in penetration testing, and how to leverage Metasploit's capabilities. Learn the structure of post-exploitation modules, including initialization, option registration, and run method implementation. Discover how to utilize post libraries, provide feedback, and store loot. Gain insights on contributing modules to the Metasploit framework, including guidelines, forking, and submitting pull requests. Enhance your understanding of advanced penetration testing methodologies and expand your cybersecurity skillset.
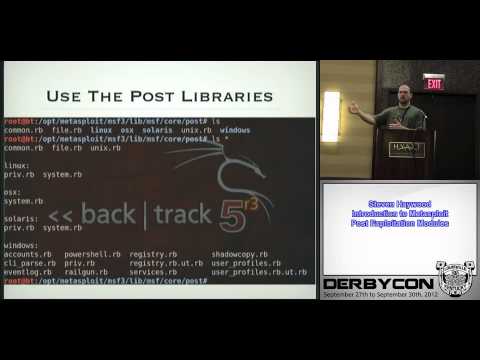
Introduction to Metasploit Post Exploitation Modules
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Ethical Hacking
#Penetration Testing
#Metasploit