Description:
Explore a novel attack technique called ShadowMove in this 51-minute conference talk by Associate Professor Jinpeng Wei from the University of North Carolina at Charlotte. Delve into the world of Advanced Persistent Threats (APTs) and learn how ShadowMove operates as a stealthy lateral movement strategy. Examine the threat model, architecture, and implementation of ShadowMove, including its components such as the Connection Detector, Socket Duplicator, Peer Handler, and Lateral Movement Planner. Analyze a case study of single-hop ShadowMove over FTP and understand how it moves among network nodes. Evaluate the stealthiness of this technique and discuss its current limitations. Gain insights into cybersecurity challenges and potential countermeasures against sophisticated attack strategies.
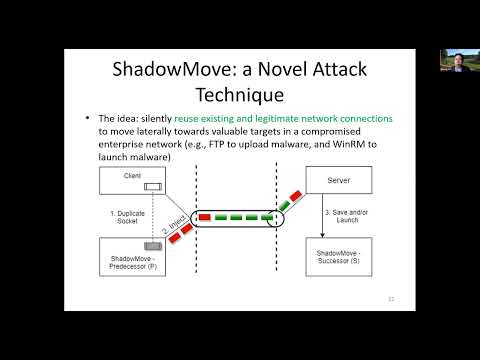
ShadowMove - A Stealthy Lateral Movement Strategy
Add to list