Description:
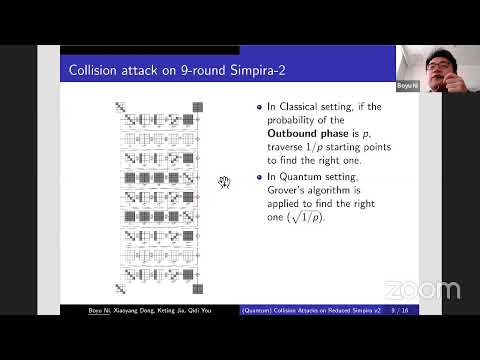
Explore hash function cryptanalysis in this 56-minute conference talk from TheIACR. Delve into KECCAK hash functions, inner collision attacks on the sponge mode, and improved preimage attacks. Learn about Hirose's Compression Function (HCF) and methods for finding collisions, including classical and quantum approaches. Examine the rebound attack assumption and its application to AES-256. Discover Grover's Algorithm, super S-box cryptanalysis, and collision attacks on Simpira variants. Gain insights into cutting-edge research on hash function security and cryptanalytic techniques.
Hash Function Cryptanalysis - Session 14
Add to list
#Computer Science
#Cryptography
#Cryptanalysis
#Quantum Computing
#Hash Functions
#Collision Attacks