Description:
Explore a groundbreaking approach to detecting Man-in-the-Middle (MitM) attacks in local area networks through a Black Hat conference talk. Discover Vesper, a novel plug-and-play MitM detector that utilizes echo-analysis techniques inspired by acoustic signal processing. Learn how ICMP echo requests can model network host connections, similar to how echoes in a cave capture environmental characteristics. Delve into the importance of MitM detection, various attack types, and the application of impulse response in LANs. Examine Vesper's functionality, including its handling of outliers, multiple intermediaries, and long-haul scenarios. Gain insights into potential adversary interference and the significance of using multiple features for detection. Conclude with an overview of the Vesper tool, its deployment, and a summary of this innovative approach to network security.
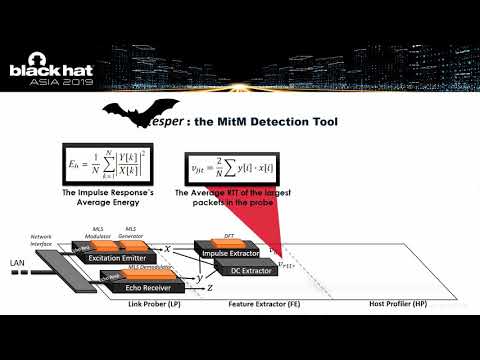
See Like a Bat - Using Echo-Analysis to Detect Man-in-the-Middle Attacks in LANs
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Network Security
#Man in The Middle Attacks
#Computer Science
#Computer Networking
#Local Area Networks