Description:
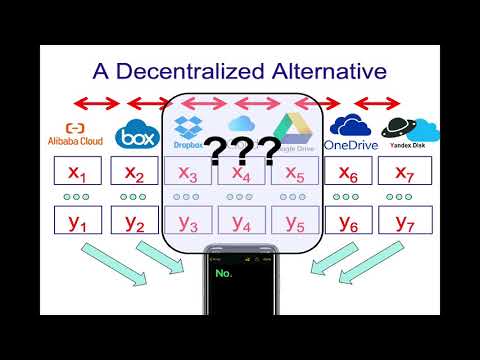
Explore secure multiparty computation in this Richard M. Karp Distinguished Lecture by Yuval Ishai from Technion Israel Institute of Technology. Delve into the challenges of storing and protecting important data in the digital age, examining solutions like encryption and secret sharing. Investigate the concept of decentralized alternatives and their potential for maintaining confidentiality while allowing data searches. Analyze the broader applications of multiparty computation, including income comparison scenarios and security concerns related to collusion. Examine the landscape of definitions, circuit-based protocols, and specific implementations like the BGW protocol and Yao's Protocol. Consider the challenges of active adversaries and hardware-based trust. Conclude by exploring open questions in feasibility, communication, and computation within the field of secure multiparty computation.
Secure Multiparty Computation
Add to list
#Computer Science
#Cryptography
#Secure Multiparty Computation
#Encryption
#Information Security (InfoSec)
#Cybersecurity
#Data Security
#Blockchain Development
#Decentralized Systems