Description:
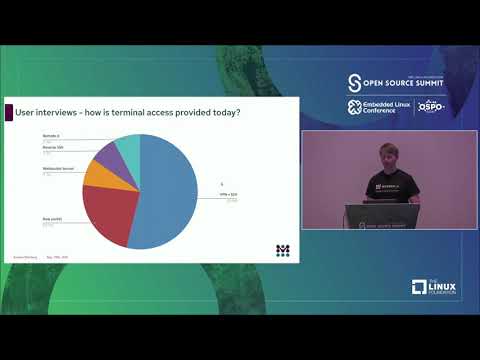
Explore common needs and approaches for remote access to IoT devices in this informative conference talk by Eystein Måløy Stenberg from Northern.tech Inc. Delve into crucial topics such as risks, audit logs, customer requests, and role-based access control. Learn about various connection methods including outbound connections, terminal access, VPN, reverse SSH, raw socket, and web socket. Discover off-the-shelf solutions and MQTT implementations. Gain insights into other use cases and compare different remote access approaches. Note that the first 10 minutes of the video lack audio due to technical difficulties.
Remote Access to IoT Devices: Common Needs and Approaches
Add to list
#Business
#Business Software
#Microsoft Office 365
#Microsoft Access
#Information Security (InfoSec)
#Network Security
#Computer Science
#Internet of Things
#MQTT
#Computer Networking
#VPN
#Role-Based Access Control
#SSH