Description:
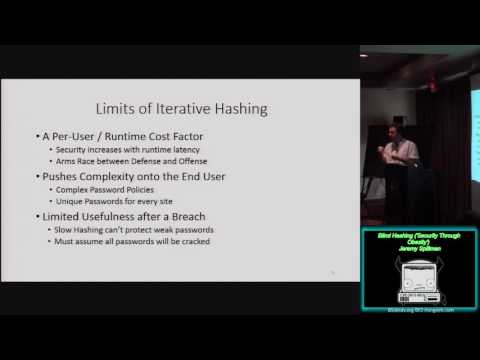
Explore the concept of Blind Hashing in this 30-minute conference talk by Jeremy Spilman at BSidesLV 2015. Delve into password security, examining attack vectors and the differences between online and offline attacks. Understand the limitations of iterative hashing and discover the goals of alternative hashing functions. Learn about the Blind Hashing technique, its pseudocode implementation, and analyze potential attacker strategies. Discuss additional challenges in password security and participate in a password game to reinforce concepts. Gain insights into offline attacks and strategies for scaling password protection systems.
Blind Hashing
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Cybersecurity
#Password Security
#Computer Science
#Cryptography
#Hashing Algorithms