Description:
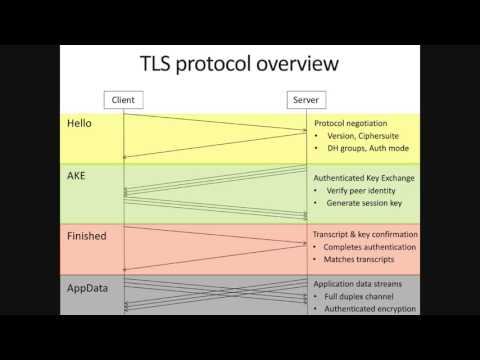
Explore the intricacies of protecting Transport Layer Security (TLS) from legacy cryptographic vulnerabilities in this comprehensive Eurocrypt 2016 invited talk. Delve into agile cryptographic protocols, attacks on legacy crypto in TLS, and the TLS protocol overview. Examine protocol agility in TLS and learn about new TLS attacks using miTLS. Investigate anonymous Diffie-Hellman (DHanon) and man-in-the-middle attacks, as well as SIGMA authenticated DH with group negotiation. Analyze the Logjam attack, including MitM group downgrade, pre-computation exploitation, and countermeasures. Study downgrade protection mechanisms in TLS 1.2 and via signatures. Explore SLOTH transcript collision attacks and their vulnerabilities. Discuss Agile AKE security goals, downgrade resilience, and test the new definition. Examine the TLS 1.3 negotiation sub-protocol, group negotiation with retry, and full transcript signatures. Understand how TLS 1.3 prevents version downgrades and achieves downgrade resilience. Conclude with final thoughts on protecting TLS from legacy cryptographic vulnerabilities.
Read more
Protecting TLS from Legacy Crypto
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Cryptography
#Network Security
#Man in The Middle Attacks