Description:
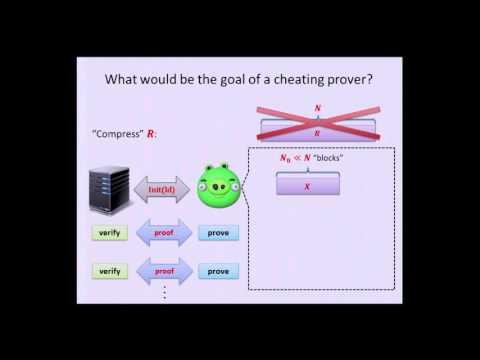
Explore the concept of Proofs of Space in this 24-minute conference talk. Delve into the general idea behind this alternative to Proofs of Work, understanding its application in dealing with Sybil attacks. Examine how to measure computational difficulty and space usage, and learn about the advantages of Proofs of Space systems. Investigate the security definitions, efficiency metrics, and potential cheating strategies. Discover the main techniques used in constructing Proofs of Space schemes, including the use of Merkle trees for commitment. Gain insights into the proof phase and the results of implementing this concept. Finally, explore the application of Proofs of Space in Spacecoin and review related work in the field.
Proofs of Space
Add to list
#Conference Talks
#Computer Science
#Cryptography
#Distributed Systems
#Data Structures
#Merkle Tree