Description:
Explore microservice security in this comprehensive conference talk that delves into securing modern architectures. Learn about tools, techniques, and considerations for protecting applications and organizations. Examine real-world examples of attacks and defense strategies, gaining insights into how to test systems for vulnerabilities. Cover essential topics such as security fundamentals, OWASP guidelines, authentication best practices, service decomposition, orchestration layer attacks, and identity management. Discover the importance of immutable architectures, auditable host configurations, and proper tool selection. Gain valuable knowledge on detection methods and log management to prevent denial of service attacks. Apply the principle of least privilege and understand the differences between roles and fine-grained permissions in microservice environments.
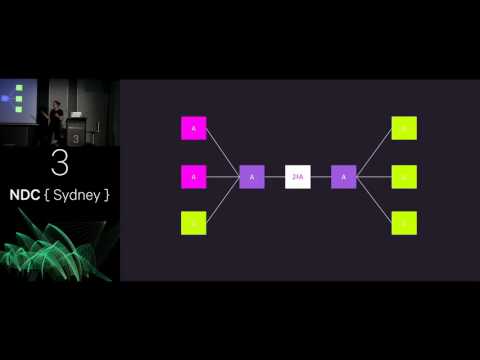
Practical Microservice Security
Add to list
#Conference Talks
#NDC Conferences
#Information Security (InfoSec)
#Cybersecurity
#Identity and Access Management
#Computer Science
#DevOps
#Log Management