Description:
Explore the potential of PowerShell for cybersecurity professionals in this comprehensive conference talk from ShowMeCon. Delve into PowerShell's growing popularity among hackers, its versatility as more than just a shell, and its powerful cmdlets for discovery, task execution, formatting, and output. Examine PowerShell providers, scripting language features, and the use of objects, variables, arrays, and logic structures. Learn about PowerShell's integration with .NET and COM, and discover how to leverage the Integrated Scripting Environment. Investigate how hackers utilize PowerShell, including techniques like PowerShell Golf and staged approaches. Gain insights into PowerShell's role in exploitation, phishing, and post-exploitation scenarios, as well as its implications for incident response and defense. Conclude with resources for further learning and a Q&A session to deepen your understanding of this powerful post-exploitation language.
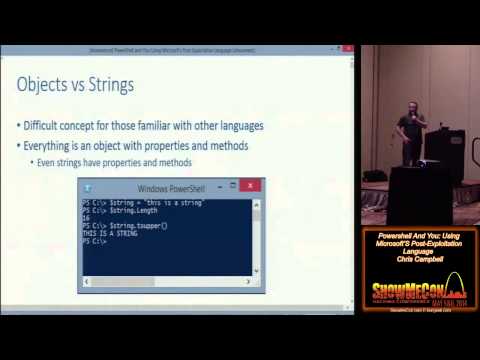
Powershell and You - Using Microsoft's Post Exploitation Language
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Ethical Hacking
#Computer Science
#Information Technology
#PowerShell
#Incident Response
#Phishing