Description:
Explore techniques and tools used by attackers to extract valuable local data during short-term physical access to a device. Learn about boot environments, password hashes, cash information retrieval, and methods for accessing data on various operating systems including Windows XP. Discover encryption practices, useful resources, and gain insights into information security concepts as presented by Louisville InfoSec.
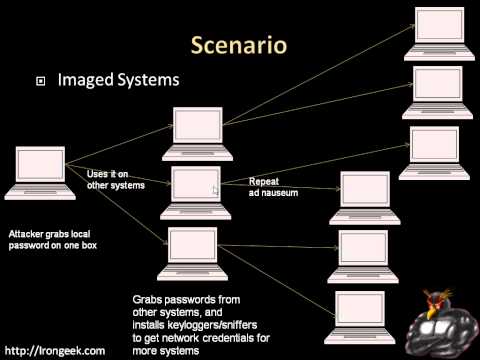
Pilfering Local Data - Attacker Strategies for Short-Term Local Access
Add to list
#Business
#Business Software
#Microsoft Office 365
#Microsoft Access
#Computer Science
#Cryptography
#Encryption
#Password Hashing