Description:
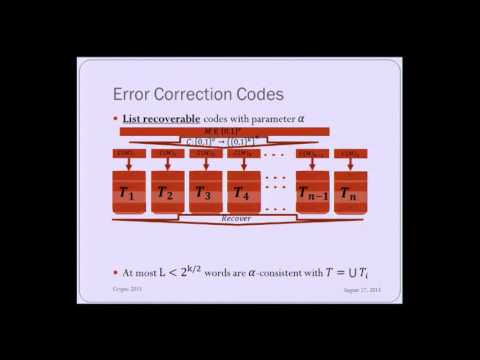
Explore the concept of parallel hashing through the lens of list recoverability in this 20-minute conference talk. Delve into the Merkle Tree Construction and the Maurer-Tessaro Scheme before examining the main results of parallel domain extension schemes. Investigate the requirements on C through attack analysis, and learn about error correction codes and list recoverable codes. Conclude by discussing applications beyond collision resistance and considering open questions in the field.
Parallel Hashing via List Recoverability
Add to list
#Conference Talks
#Computer Science
#Cryptography
#Information Security (InfoSec)
#Cybersecurity
#Data Security
#Hashing Algorithms