Description:
Explore the intricacies of Server-Side Request Forgery (SSRF) attacks and their implications in cloud environments in this 31-minute conference talk from 44CON Information Security Conference. Delve into the OWASP definition of SSRF, understand cloud metadata, and examine basic examples and CVE cases. Navigate through SSRF hurdles, including headless browsers and HTML renderers. Discover techniques like simple XSS via wkhtmltopdf and advanced methods for bypassing security measures. Learn about WeasyPrint vulnerabilities and the power of source code analysis. Investigate DNS rebinding and HTTPRebind for enhanced attack vectors. Gain valuable insights into cloud security and SSRF mitigation strategies from security expert Cody Brocious.
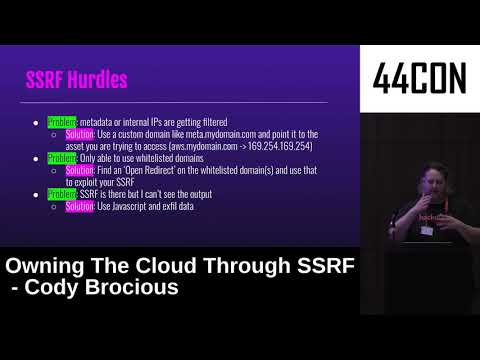
Owning the Cloud Through SSRF
Add to list
#Conference Talks
#44CON
#Information Security (InfoSec)
#Ethical Hacking
#Server-Side Request Forgery (SSRF)
#Programming
#Web Development
#Web Application Security
#Cloud Computing
#Cloud Security