Description:
Explore a novel web hacking technique that bypasses most XSS mitigations in this 42-minute conference talk from OWASP BeNeLux Day. Delve into the concept of script gadgets, legitimate JavaScript pieces that can be exploited to circumvent HTML sanitizers and security policies. Examine case studies and real-world examples demonstrating the inadequacy of current mitigation techniques for modern applications. Learn about the prevalence of these gadgets in popular JavaScript libraries, APIs, and applications. Understand the methodology behind bypassing Web Application Firewalls, XSS filters, HTML sanitizers, and various Content Security Policy implementations. Analyze empirical study results, root causes, and challenges associated with script gadgets. Gain insights into the need for more preventive mechanisms in web security and the limitations of current XSS mitigations.
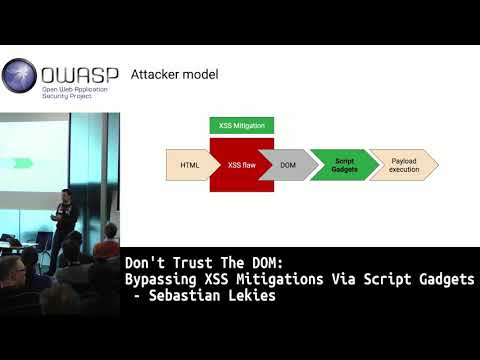
Don't Trust the DOM - Bypassing XSS Mitigations via Script Gadgets
Add to list
#Conference Talks
#Information Security (InfoSec)
#Ethical Hacking
#Cross-Site Scripting (XSS)
#Cybersecurity
#Web Security
#Content Security Policy (CSP)