Description:
Save Big on Coursera Plus. 7,000+ courses at $160 off. Limited Time Only!
Grab it
Explore vulnerability scanning in Kubernetes clusters and learn effective security measures in this comprehensive conference talk. Discover how to audit technical configurations, identify vulnerabilities, and apply patches to critical components. Delve into exploiting Kubernetes primitives for implementing robust security mechanisms, including RBAC, AdmissionController, NetworkPolicy, and SecurityContext. Enhance cluster security with Open Policy Agent for finer control and integrate Falco for detecting suspicious actions within containers and at the API Server level. Learn to implement a CI/CD pipeline with Clair for vulnerability analysis during image builds. Gain insights into penetration testing, package discovery challenges, vulnerability databases, and automating decision processes. Understand the complexities of container results, issues with specific components like libcurl and Busybox, and explore solutions such as VEX (Vulnerability Exploitability eXchange) for more accurate vulnerability assessments.
Read more
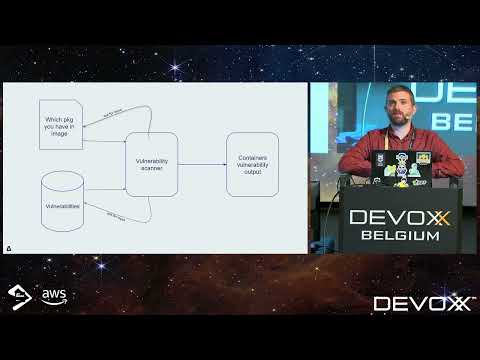
Overcoming CVE Shock - Adding Perspective in Vulnerability Scanning
Add to list
#Conference Talks
#Devoxx
#Information Security (InfoSec)
#Penetration Testing
#Computer Science
#DevOps
#CI/CD Pipelines
#Kubernetes
#Kubernetes Security
#Cybersecurity
#Vulnerability Scanning
#Programming
#Cloud Computing
#Cloud Security
#Open Policy Agent
#Operating Systems
#eBPF
#Falco