Description:
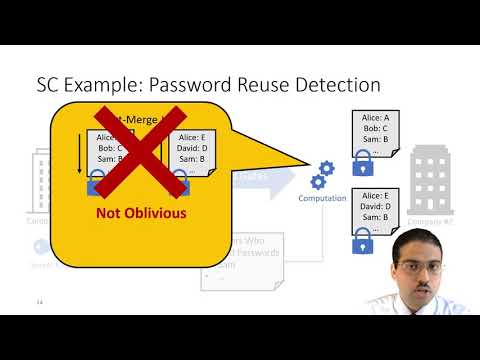
Explore a 15-minute conference talk from OSDI '21 that introduces MAGE, an execution engine for Secure Computation (SC) designed to efficiently run SC computations that exceed available memory. Learn about the challenges of memory overhead in SC, the concept of memory programming, and how MAGE leverages the oblivious nature of SC schemes to create a highly efficient virtual memory abstraction. Discover how MAGE outperforms traditional OS virtual memory systems and enables SC computations to run at nearly the same speed as if unlimited physical memory were available. Gain insights into the workflow, implementation, and evaluation of MAGE, including its application in password reuse detection and potential uses in various industries adopting SC for data privacy and security.
MAGE - Nearly Zero-Cost Virtual Memory for Secure Computation
Add to list
#Conference Talks
#OSDI (Operating Systems Design and Implementation)
#Computer Science
#Cryptography
#Secure Computation
#Memory Management