Description:
Explore a 20-minute conference talk from OSDI '20 that presents Ward, a novel kernel design addressing the performance penalties associated with mitigating transient execution side-channel attacks like Meltdown and Spectre. Learn about the unmapped speculation contract and how it enables many system calls to execute without mitigation overhead. Discover how Ward's separate kernel page table for each process improves performance compared to standard designs with mitigations, ranging from a few percent to several factors depending on the hardware generation and system call. Gain insights into the implementation in the sv6 research kernel, related defense strategies, and open questions in the field of transient execution attack mitigation.
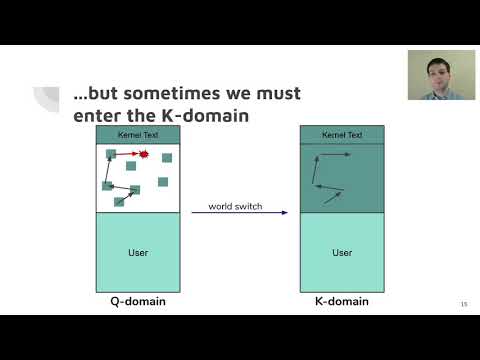
Efficiently Mitigating Transient Execution Attacks Using the Unmapped Speculation Contract
Add to list
#Conference Talks
#OSDI (Operating Systems Design and Implementation)
#Programming
#Software Development
#Information Security (InfoSec)
#Cybersecurity