Description:
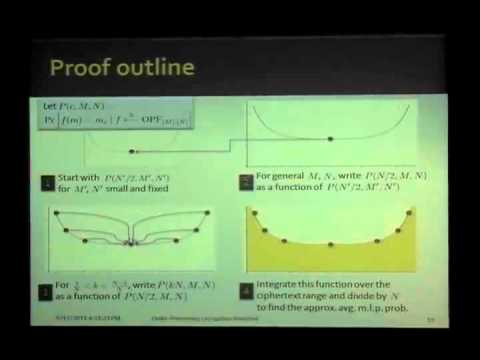
Explore order-preserving encryption (OPE) in this 20-minute talk from Crypto 2011. Delve into improved security analysis and alternative solutions presented by Alexandra Boldyreva, Adam O'Neill, and Nathan Chenette. Learn about OPE applications in range queries on encrypted data, cryptographic studies, and security guarantees of ideal objects. Discover new security notions, including window distance one-wayness and ROPF one-wayness. Examine proof strategies and outlines for ROPF security considerations. Investigate modular OPE and committed OPE as alternative solutions. Gain insights into the latest advancements in order-preserving encryption and its implications for data security.
Order-Preserving Encryption Revisited: Improved Security Analysis and Alternative Solutions
Add to list