Description:
Explore the concept of Hierarchical Identity-Based Encryption in this Eurocrypt 2016 talk by Mohammad Mahmoody and Ameer Mohammed. Delve into the intricacies of Identity-based Encryption security definitions and examine black-box separations. Learn about compression techniques, including GT01, and understand the challenges of IBE adaptive security. Analyze issues such as adversaries asking inversion queries and choosing identities. Gain insights into how these elements interconnect to form a comprehensive understanding of Hierarchical Identity-Based Encryption's power and potential applications in cryptography.
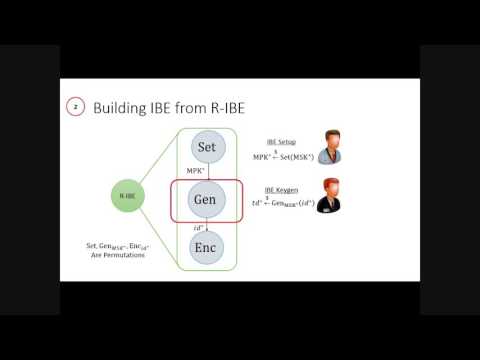
On the Power of Hierarchical Identity-Based Encryption
Add to list
#Conference Talks
#Computer Science
#Cryptography
#Information Security (InfoSec)
#Cybersecurity
#Adaptive Security