Description:
Explore the groundbreaking discovery of Remote Direct Memory Access (RDMA) Turing completeness in this 18-minute conference talk from NSDI '22. Dive into RedN, a novel approach for implementing complex RDMA offloads without hardware modifications, using self-modifying RDMA chains. Learn how this technique lifts the existing RDMA verbs interface to a Turing complete set of programming abstractions, enabling offload of complex tasks like key lookups in distributed systems. Discover the potential performance improvements, including reduced latency for key-value get operations, enhanced performance isolation, and failure resiliency. Gain insights into the evaluation of RedN, its application in Memcached lookups, and the significant latency reductions achieved in both normal and contentious scenarios.
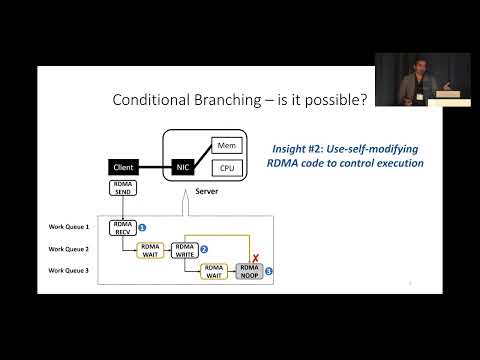
RDMA Is Turing Complete, We Just Did Not Know It Yet
Add to list
#Conference Talks
#USENIX Symposium on Networked Systems Design and Implementation (NSDI)
#Computer Science
#Distributed Systems
#Database Management
#Memcached