Description:
Explore advanced techniques for discovering zero-day vulnerabilities in enterprise web applications in this conference talk from NahamCon2022. Delve into the intricacies of HCL Digital Experience, IBM Websphere Portal, Lotus Domino, Solarwinds Web Help Desk, and Sitecore's Experience Platform. Learn how to decompile JARs, identify attack surfaces, chain vulnerabilities, and craft exploits for post-auth RCE via directory traversal. Gain insights on variant hunting, super SSRF, and leveraging hardcoded credentials in development and production environments. Master the art of source code analysis, payload crafting, and encryption key retrieval to enhance your offensive security skills.
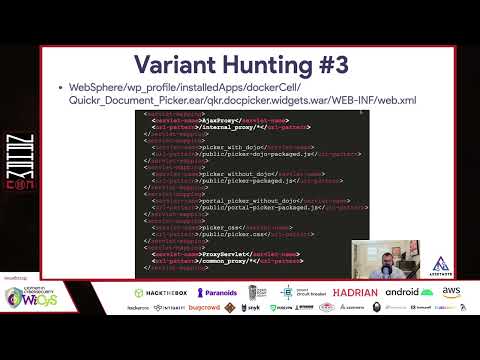
Finding 0days in Enterprise Web Applications
Add to list
#Conference Talks
#NahamCon
#Information Security (InfoSec)
#Ethical Hacking
#Server-Side Request Forgery (SSRF)
#XML External Entity (XXE) Injection
#Programming
#Web Development
#Web Application Security
#Cybersecurity
#Zero-Day Vulnerabilities
#Attack Surface Analysis