Description:
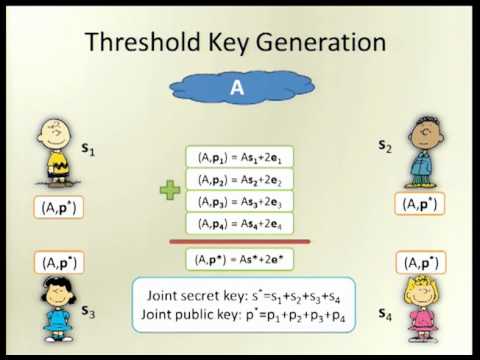
Explore a conference talk from Eurocrypt 2012 on multiparty computation techniques with reduced communication and computational requirements. Delve into the authors' innovative approach using fully homomorphic encryption (FHE) and threshold FHE for secure multi-party computation. Learn about the advantages of FHE in 2-party computation, including input encryption, homomorphic evaluation, and cloud delegation. Examine the Learning with Errors (LWE) assumption and its key-homomorphic properties. Discover the intricacies of threshold key generation, basic LWE-based encryption homomorphism, and evaluation keys. Understand the multi-round process of threshold key generation and its application in threshold FHE. Investigate the proposed MPC protocol and its extension to malicious adversaries. Gain insights into cutting-edge cryptographic techniques for secure multiparty computation with enhanced efficiency.
Multiparty Computation with Low Communication
Add to list
#Computer Science
#Cryptography
#Fully Homomorphic Encryption
#Secure Computation
#Information Security (InfoSec)
#Cybersecurity
#Privacy-Preserving Technology