Description:
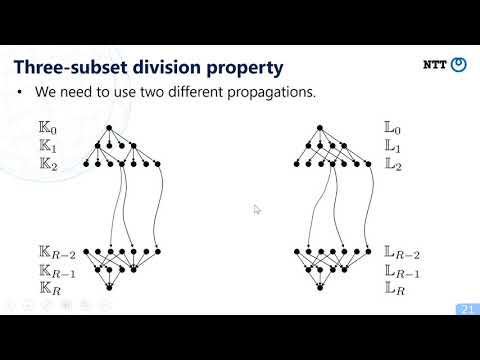
Explore a comprehensive presentation on advanced cryptographic techniques focusing on improved cube attacks using modeling for three-subset division property without unknown subset. Delve into the evolution of cube attacks, from their origins as variants of higher-order differential attacks to the latest third-generation methods. Examine the paper's key findings, including degeneration results for stream ciphers and the challenges of implementing three-subset division property in MILP. Learn about the new modeling approach and its application in a successful 839-round key recovery attack against Trivium. Gain insights into the cutting-edge research presented at Eurocrypt 2020, advancing the field of cryptanalysis and cipher security.
Modeling for Three-Subset Division Property Without Unknown Subset - Improved Cube Attacks
Add to list