Description:
Explore the intricacies of Oblivious Transfer (OT) Extension in this 23-minute conference talk. Delve into the fundamentals of OT, compare various extension techniques, and examine passive security considerations. Learn about correlation errors, hashing steps, and implementation improvements. Discover how to achieve one billion OTs with 2 Gbit/s throughput, ultimately understanding why "The Pipe is the Limit" in this advanced cryptographic discussion.
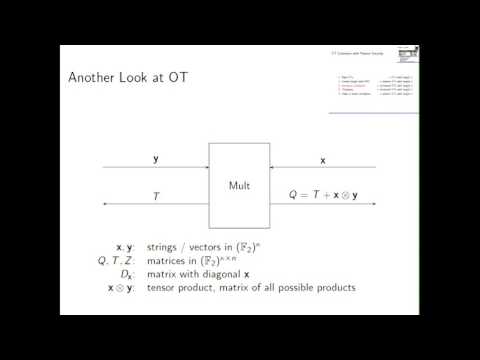
Malicious for Free OT Extension - The Pipe is the Limit
Add to list
#Conference Talks
#Computer Science
#Cryptography
#Oblivious Transfer
#Information Security (InfoSec)
#Cybersecurity
#Privacy-Preserving Technology