Description:
Explore a comprehensive conference talk on maturing information security beyond compliance standards. Delve into Joey Smith's personal experiences and professional insights as he discusses the evolving attack surface, business alignment challenges, and the limitations of traditional compliance models. Learn about a strategic approach to security maturity, including timelines, social engineering tactics, access control, and identity management. Discover practical strategies for policy enforcement, on-net vs. off-net security considerations, and the implementation of an Information Security Operations Center. Gain valuable knowledge on enhancing security awareness and the importance of recognizing and rewarding security-conscious behavior within organizations.
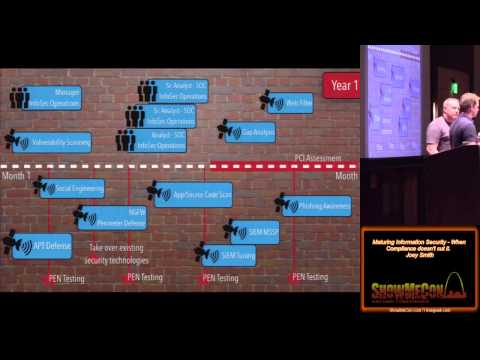
Maturing Information Security When Compliance Doesn't Cut It
Add to list
#Conference Talks
#Information Security (InfoSec)
#Ethical Hacking
#Social Engineering
#Business
#Corporate Governance
#Compliance
#Cybersecurity
#Access Control
#Identity Management
#Security Awareness