Description:
Explore insider threat detection and automation through behavior analytics in this 23-minute OWASP Foundation talk. Delve into the importance of insider threat detection, types of insiders, and User and Entity Behavior Analytics (UEBA). Learn about anomalies, volumetric analysis, and statistics in threat detection. Discover use cases, including identity theft, and examine models, data analytics, and technology used in this field. Gain valuable insights from a case study and a comprehensive overview of insider threat detection strategies.
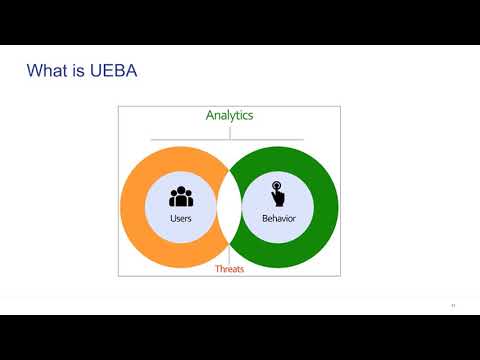
Insider Threat Detection & Automation by Behaviour Analytics
Add to list
#Conference Talks
#Mathematics
#Statistics & Probability
#Information Security (InfoSec)
#Cybersecurity
#Data Science
#Data Analytics
#Identity Theft