Description:
Delve into the advanced concepts of indistinguishability obfuscation in this second part of a comprehensive lecture series. Explore well-founded assumptions that form the basis for this cryptographic technique, gaining insights into its theoretical foundations and practical implications. Examine the latest research developments and potential applications in secure computation and cryptography.
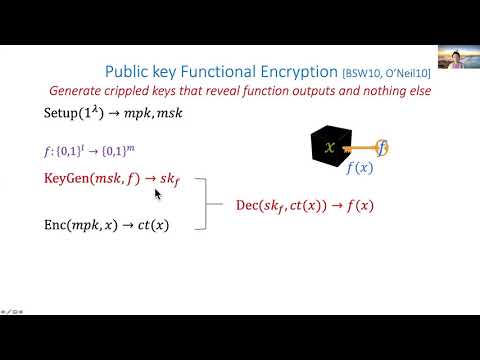
Indistinguishability Obfuscation from Well-Founded Assumptions - Part 2
Add to list
#Computer Science
#Cryptography
#Secure Computation
#Theoretical Computer Science
#Indistinguishability Obfuscation