Description:
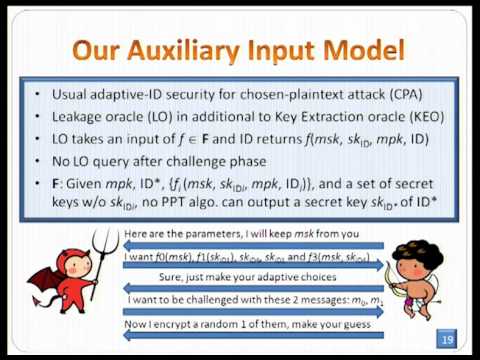
Explore a talk from Eurocrypt 2012 on Identity-Based Encryption resilient to continual auxiliary inputs. Delve into the authors' research on side-channel attacks, leakage restrictions, and the bounded retrieval model. Learn about IBE with auxiliary inputs, the problem statement, and key contributions including the modified Goldreich-Levin Theorem. Examine the auxiliary input model, construction roadmap, and scheme intuitions. Discover extensions like leakage during setup and gain a comprehensive understanding of the authors' contributions to this cryptographic field.
Identity-Based Encryption Resilient to Continual Auxiliary Inputs
Add to list
#Computer Science
#Cryptography
#Information Security (InfoSec)
#Cybersecurity
#Side Channel Attacks