Description:
Explore the world of exploit kits in this 36-minute conference talk from Derbycon 2016. Dive into the infection process, challenges in collecting data on exploit kits, and the innovative Maxwell architecture. Learn about whitelist examples, virtual machine configurations, and anti-researcher techniques. Discover post-processing methods and how to integrate all components effectively. Gain valuable insights into this critical aspect of cybersecurity, complete with references for further study.
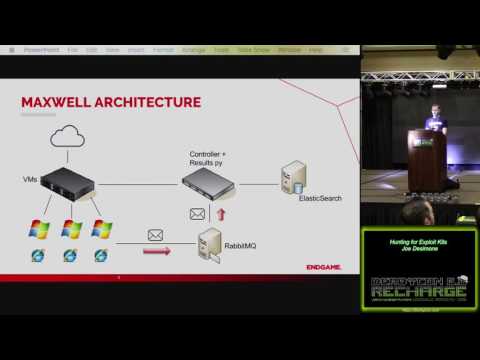
Hunting for Exploit Kits
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Computer Graphics
#Post-Processing
#Exploit Kits