Description:
Explore two strategies for supply chain attacks in this Hack In The Box Security Conference talk. Delve into the BARIUM APT group's tactics, techniques, and procedures (TTPs) used in various supply chain attacks, including the ASUS Operation ShadowHammer. Learn about the group's targeting of game and software development companies worldwide, their use of 'winnti' and 'PlugX' malware, and the Korea Internet & Security Agency's analysis of related incidents. Discover how attackers compromise software development environments and update servers to execute these sophisticated attacks. Gain insights from experienced cybersecurity professionals on intrusion analysis, malware detection, and defensive strategies against supply chain threats. Examine multiple case studies, explore the ATT&CK Matrix, and understand the importance of securing software development and distribution processes.
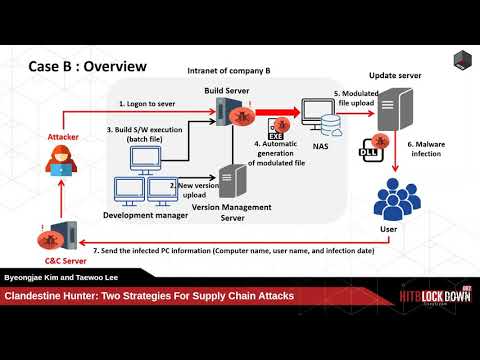
Two Strategies for Supply Chain Attacks
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Cybersecurity
#Malware Analysis
#Supply Chain Attacks