Description:
Explore an in-depth analysis of Operation SemiChimera, a series of advanced persistent threat (APT) attacks targeting the semiconductor industry, particularly in Taiwan. Delve into the tactics, techniques, and procedures used by the threat actors, their potential motivations, and the devastating impact of stolen intellectual property. Gain valuable insights into the current cybersecurity landscape of Taiwan's semiconductor sector and learn from the experiences of companies that have improved their defenses. Understand the challenges facing the industry and discover practical strategies to protect against similar attacks. This presentation, delivered by cybersecurity experts from Cycraft, offers crucial information for semiconductor companies and security professionals looking to enhance their threat intelligence and defensive capabilities.
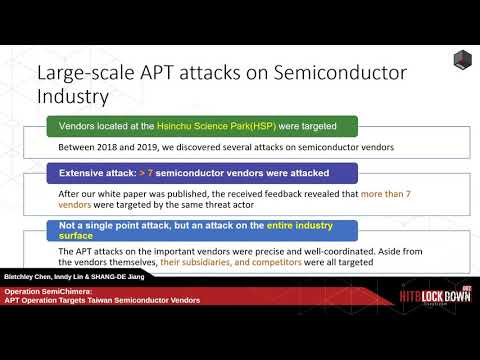
Operation SemiChimera
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Cybersecurity
#Business
#Management & Leadership
#Quality Management
#Root Cause Analysis